Telegram was launched in 2013 and has since become one of the most widely used messaging apps. Some people use Telegram to communicate with family and friends, while others use it to stay informed in group chats or channels, where one or few people can broadcast content to millions of subscribers.
It allows you to send self-destructing messages, post huge files, create and interact with bots, start end-to-end encrypted voice and video calls, and do most things that you can expect from a messaging app, like sending audio messages, stickers and emojis.
So what's wrong with Telegram? Well, it dangerously gives some people a false sense of privacy that is in no way warranted. This is mainly due to misleading advertising: Telegram claims to be open source and heavily encrypted. Even if these deceptive statements were truth, the popular messaging app has other serious issues that compromise your privacy.
Closed-source, centralized and not encrypted: a privacy nightmare
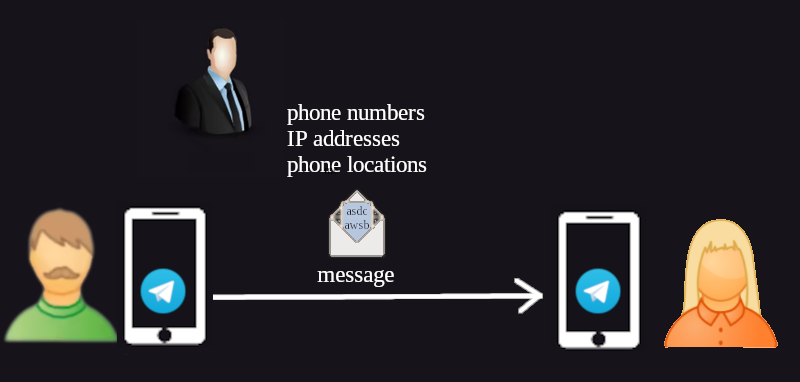
Only the Telegram client code is open source, but that code is useless without the back-end closed-source programs and infrastructure. Those core components are controlled by a single company that can be easily forced to comply with authorities. In August 2024, Telegram CEO was arrested by French authorities who demanded information on users of the app. He gave in, showing the world that your private conversation, phone number, IP address, pictures and so on are not safe.
Telegram's funding depends on paid subscriptions that unlock special features and ads. Who can assure you that in the future they will not expand their revenue streams by offering you ads based on the things you send or training AI?
What prevents Telegram employees, hackers or government agents from reading your messages? Nothing. Messages on Telegram aren't encrypted by default, so users are in the buff. Sure, They could start a "secret chat", which is quite inconvenient, as you have to tap various buttons to access this option and wait for the other user to connect before you can send messages. To add insult to injury, that feature is not available on desktop or web clients and its usage would surely raise suspicion. Optional privacy makes users who opt in stand out in the crowd.
You will be tracked
Forget about being anonymous on Telegram. Before you can even start chatting you have to provide a phone number, which can easily be linked to your real identity. As a solution, you could use a burner phone and use Telegram on your computer, but what if you want to use it on a mobile phone? You would have to be tech-savvy enough to install a privacy-friendly mobile operating system and avoid being tracked by mobile phone networks.
One way to protect your identity is to pay for a remote SMS verification with Monero (SMSpool offers this service) and use Telegram on a free operating system. If you are afraid that Telegram might ask for verification again and you want to keep using the same account, you can buy or long-term rent a mobile number that is not related to your identity.
In short, using Telegram for privacy or anonymity is overly complicated, so it is not recommended for those purposes. If someone invites you to use Telegram to talk about sensitive topics, avoid entering the lion's den. Instead tell them to do it in person or use an open source, decentralized and anonymous alternative (such as SimpleX, Delta Chat or Briar).